The Request Relay is a BugPoC feature that lets you easily chain a server callback into your Front-End or Python PoCs.
Some complicated bugs require Out-of-Band (OOB) communication with an attacker-controlled server. This server typically listens for inbound HTTP requests that leak sensitive values from the victim. Oftentimes this value then needs to be used in the next step of the attack chain.
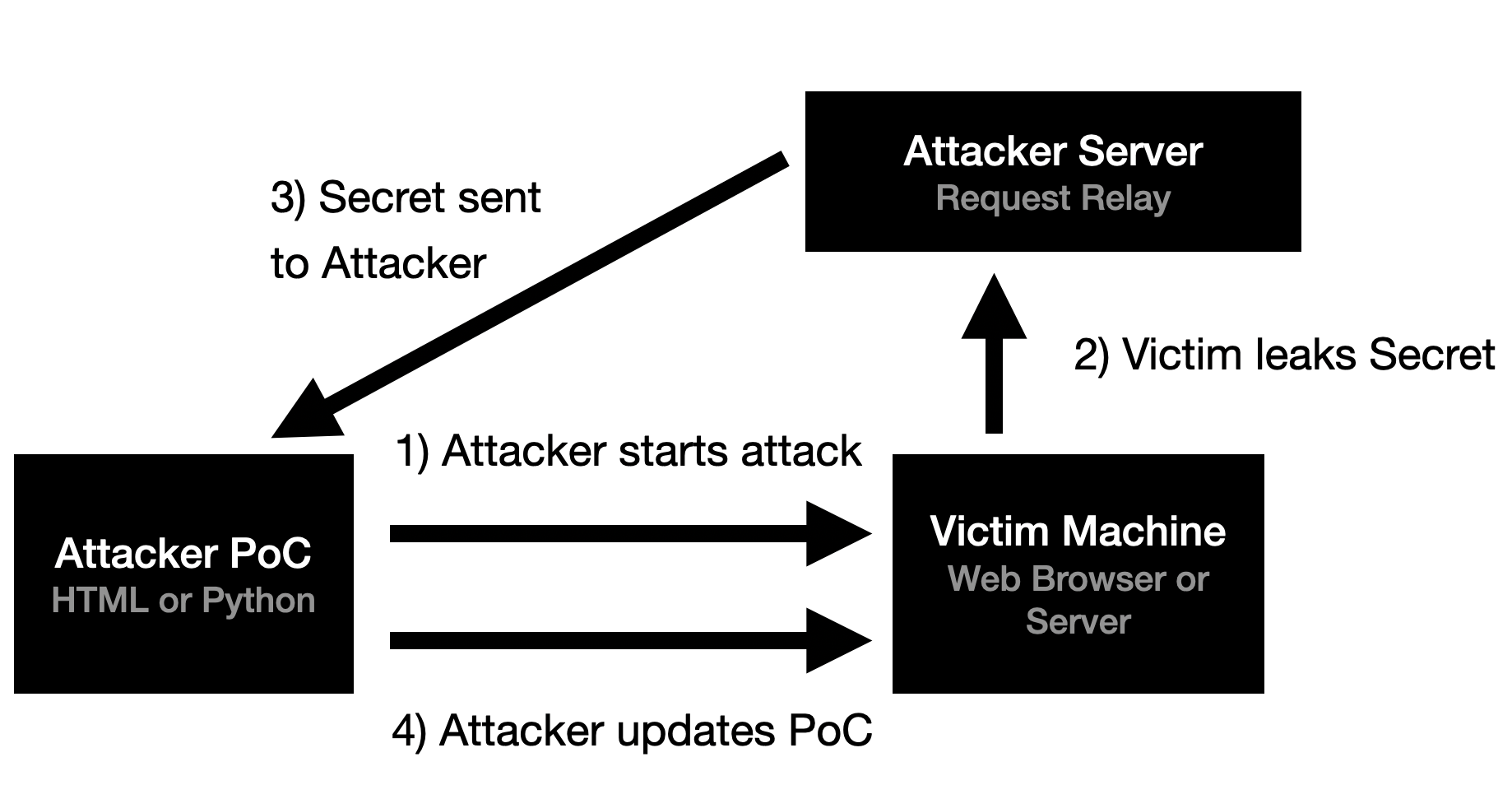
A Web App example of this style of attack is a CSRF PoC that uses CSS Injection to exfiltrate the CSRF token. An API / WebService example is a blind SSRF bug that leaks a server-secret in a custom header. Before BugPoC, building a working demo for these types of bugs was tediuous and error-prone.
The BugPoC Request Relay simplifies this process by dynamically generating a custom endpoint that automatically relays the HTTP request back to your Proof-of-Concept. With the help of our JavaScript and Python libraries, you can easily integrate a Request Relay into your PoC. No need to setup or maintain a Callback Server for OOB communications.
|
Front-End Example
|
Python Example
|